Celebrate!
OpenID Connect 1.0 Final is here!
After four and half years, or six years if we include the time needed to start the working group, finally, OpenID Connect is released as final.
Like I have been explaining many times in this blog, OpenID Connect is something that forms “the identity layer” on the internet. Let me explain.
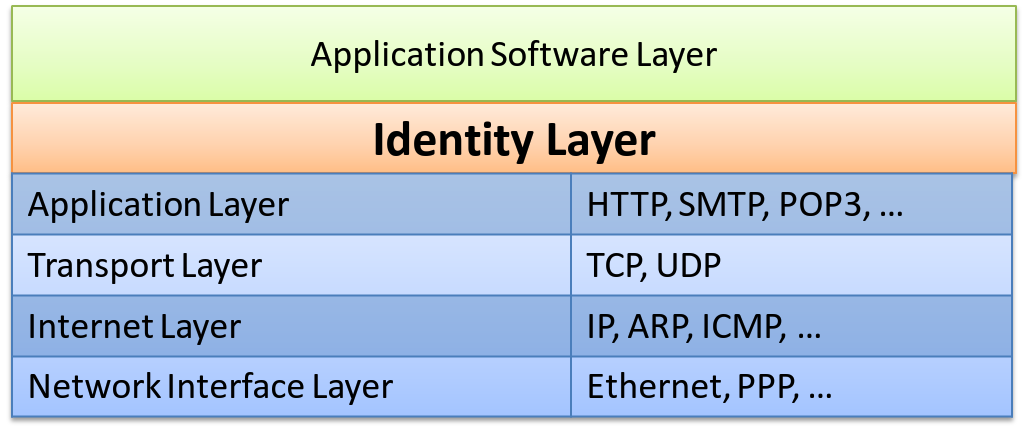
When we speak of “Layers”, we often use something called TCP/IP reference mdoel. This is a model which that defines the communication functionality (communication protocols) that an internet host should have into 4 layers, and is often called as TCP/IP Reference Model or the Internet Protocol Suites (RFC1122) . The layer 4 is called application layer but this “application” means communication services such as HTTP and FTP and does not mean the application software that we use. The application software is built on top of them. It can be depicted as below.

In the Fig.1, I have depicted the “Identity and Access Management (IAM)” also known as “Authentication/Authorization functionality” in ellipses. The reason I specifically brought it up among other functionality is that it exists in every application software in one form or another.
And it is said that over 95% of the security breaches in the internet is caused by this functionality being not properly implemented. In a meeting last week, Dr. Peter Tippet told us that a little improvement in the identity far surpasses the effect of perfecting all the other security measures such as firewall and anti-virus.
What we have released at this time are international standards that pulls out the functionality into another layer – Identity Layer – and enables software applications to outsource the authentication and authorization to an external module with a standard interoperable interface. It can be roughly depicted as in Fig. 2.

Here, Application Software talks to the Identity Layer[1] through well defined standard protocol to achieve “Authentication and Authorization” safely. By extracting the authentication and authorization functionality and outsourcing it to a special purpose software or service, the application software can specialize on what they are supposed to do – the application functionality – the core competence – without implementing authentication and authorization which is extremely hard to implement correctly, thus, without building the security holes into itself.
What we have released at this time as final are these four specifications.
| OpenID Connect Core | The core of the identity layer. One can achieve authentication and authorization just by implementing this specification. |
| OpenID Connect Discovery | Enables the client to find out the relevant endpoint for the user. |
| OpenID Connect Dynamic Registration | Enables the client to register to the server dynamically. |
| OAuth Multiple Response Type | Defines some of the messages that the above uses. |
OpenID Connect is supported by many companies. For example, Google’s g+ login system actually is OpenID Connect now and has announced that phasing out other protocols by April 2015. Microsoft and Salesforce has already implemented it as well. In Japan, Nomura Research Institute has provided the functionality as a backend technology provider to many companies, and such services like Yahoo! Japan and Softbank (the parent company of the Sprint, US) has it already in production. Other companies like ForgeRock, CA, VMWare, AOL, Cisco etc. also announced or has implemented it in some form or another.
In addition, in the Mobile World Congress 2014 (MWC2014) in Barcelona, GSMA announced “Mobile Connect“, which is a profile of OpenID Connect for the mobile network operators. (I will follow up on it by another blog post.)
There are open source implementation of OpenID Connect as well. For example, Nomura Research Institute has released the phpOIDC: an open source project of OpenID Connect (OIDC) in PHP, today as a part of PEOFIAMP project. You can find it here: https://bitbucket.org/PEOFIAMP/phpoidc. Other open source implementations includes MITREid Connect (java), which was developed by Mitre Corporation and given to MIT-KIT, OX OpenID Connect Platform by Gluu (java), Nov Matake’s ruby openid_connect, Roland Hedberg’s pyopenid (python), and so on.
OpenID Connect is the result of a lot of effort of many people. I would like to take this opportunity to thank all of those who put in their support to this work.
Nat Sakimura
[1] I have simplified it as “Identity Layer”, but it actually includes the layer that issues the tokens that represents the access rights, the “identity layer” that exchanges identity data (attributes that are related to an entity), and the access control layer that performs actually access control using it.
Hi Nat! I’m doing a research of OpenID Connect for my Career Final Project and I have 2 options: The first is to add more functionality to OpenID by implementing a Two way authentication system, do you think it is possible? The another idea is to develop an OpenID version for other services that are not web, like SSH or another. I will apreciate your opinion. Thank you!