First of all, let me state an important assumption.
Whether you or me, or the PC that I am writing this blog post, let us assume that they exist and not get into a philosophical issue of existence. Let such existing bodies be called “Entity”.
Thus, I am an entity, this PC is an entity, etc.
Note that we cannot recognize them directly. We have to observe them through the cognitive process of the observer. Therefore, even for yourself, there are such things as “self recognition” of yourself and “3rd party recognition” of yourself.
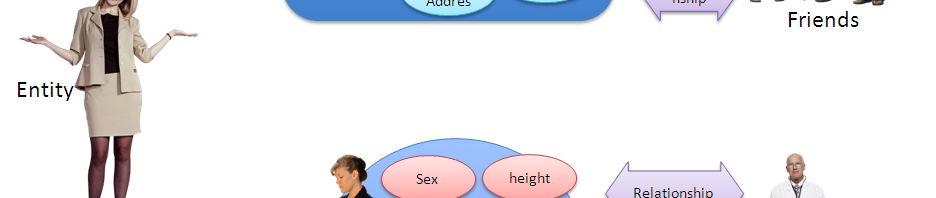
Figure 1 depicts this relationship.

In this figure, the left most “entity” is you (*1).
You live in a society and have relationship with many people. In Figure 1, frends are depicted in the top right, and your boss is depicted in bottom right. You obviously have many more relationship but the space limitation allowed me to write only two of them.
You have an expectation on your self-image, i.e., “how you want to be recognized”, by these entities. Such self-image is called an “identity”.
Note that such “self-image/identity” is an abstract concept and neither you or your friends can observe directly. In reality, they see-feel-hear your looks, your cloth, what scent you wear, what you say, where you live, who is your boy friend, what phone you use, etc., i.e., your “attributes”, and perceive your “identity”. In another word, “self-image/identity” is formed by those attributes. (This is an important point to remember when you talk about privacy.) Accordingly, ISO/IEC 24760 defines “identity” as “set of attributes related to an entity”. Thus, “Digital Identity” is set of digitized attributes so that computers can deal with it.
Note that identifiers like Employee number or SSN are just another attribute. Many people think of them as really special thing, but they are not.
“3rd party recognition” and “self recognition”: interpersonal problems
The “self-image/identity” cannot be formed directly, as it is stated above. They are formed by sharing/providing various “attributes” to the entities (including yourself.) For example, to create “Lively and Friendly Image”, you could ware sporty attire, talk loud and fast, joke often, use very friendly nickname, etc. towards your friends.
The image that others gets from these attributes depends on the receiver, so it is not possible to perfectly match the “3rd party recognition” of yourself with your “self recognition”. There always are some “delta”. For example, you were trying to create an image that is lively and friendly, but your boy friend may perceive it as being a “rattlebrain” and may say “good-bye.” How despairing that would be for you!
This difference/delta between the “self-recognition” and “3rd-party-recognition” on your “self-image/identity” constitute a large part of suffering of human being. And the right to control this delta relates closely to your right of privacy.
Privacy Rights
Let me note that “privacy rights” are yet to find consensus in many jurisdiction. I am merely stating here the notion of it among some faction of the researchers in Digital Identity field. (In Japanese law, it is basically the same with what is called as “self-image control right” proposed by Prof. Munesue.)
As I have depicted in the figure 1, an individual/entity uses multiple “self-image/identity”. Suppose that currently, you are in a state that is working well. You are recognized by your friends as you want it to be, and you are recognized by your boss as you want it to be. Your “self-image” towards each of them and “their-image” matches pretty closely. Your relationship with these people are in good shape, you keep your dignity, and you are feeling happy about it. You have right to seek the dignity and the happiness, at least, according to the article 13 of the Japanese Constitution. So here is the definition by Prof. Munesue.
“Privacy is the right to use various self-image according to the multiplicity of social relationship that can be formed” (Munesue, “New Structure for the Human Right”, Shinzan Publication (1992) PP.187-195.
Now, suppose that an evil person, Eve came in and provided some information that you provided to your boss but not to your friend to your friend. If you are lucky, the friend’s recognition about you would not change, but in many cases, it would. As the result, the relationship with your friends may deteriorate. This is called the “Privacy Infringement.”
In the model depicted in figure 1, an act of taking out an attribute from an identity and adding it to another would constitute the privacy infringement. The reason that PII leakage incident are often called as privacy breach comes from this fact. Such incident is actually adding attributes that was shared with an entity to the “public identity”.
Note that PII leakage and Privacy Infringement/Breach are two distinct notion. The former is just a possible cause of the later.
Access Control
Now we understand that it is useful to provide attributes to a certain entity to create a desired self-image. At the same time, we now understand that providing such attributes to another entity would constitute a privacy infringement.
Digital Identity is a set of attributes that were provided to an entity. To avoid the privacy infringement, we have to make sure that only the intended entity gets access to the attributes. This implies that we need to identify the receiver and implement access control to the access to the digital identity.
This act of identification of an entity at some degree of certainty is called “authentication.” The degree of certainty is often called as “assurance level.” Authorization is the act of allowing such identified entity or service to access the give set of attribute (=digital identity). Who has the right to authorize depends on the cases. Such authorizing entity must also be authenticated before granting the access.
Thus, access authorization actually consists of:
- Authentication of the accessing entity.
- Authentication of the authorizing entity.
- Authorization.
- Access to the digital identity.
Time is up for now. I will continue this in the coming blog posts.
(*1) Although this post deals with natural human entity, an entity could be anything else. It could even be an imaginary one. In the NSTIC context, smart meter is often referred to as being and entity that has “digital identity”.
Nat, your write up is missing a crucial distinction. It is founded in the very premise that there is a reason you wrote this piece. Your conceptualization of identity is rooted in administrative process. But “I” precede any and all administrative process. This is crucial to understanding the missing link in our approach to identity administration.
I exist pre-identity. I exist pre-system management. I exist pre-citizenship. I exist pre-market.
I am a sovereign source authority. I am edge-driven. I am the only resilient component of the Human species… I am an Individual sentient entity.
ID[entity] Sovereign Source Authority [entity]ID is the verbal structure that must be set in motion.
Identity is a function of all the things you have stated, and more, but unless we structure use in a manner that reflects inherent value leverage, we will continue to solve the wrong problems.
The data-verse is account-centric. Institutions the world over are under direct pressure to reconstitute the relationships that Individuals have with entities. These relationships are structured across the board to mimic the structure of socio-economic participation. In an account-centric data-verse, sovereign source is a blatant omission. Any discussion of identity without it is fatally flawed.
The battlefield is edge-driven. Resilient communities are edge-driven. The market will be edge-driven.
ID[entity] Sovereign Source Authority is an edge-driven governance model.
http://www.moxytongue.com/2011/10/identity-sovereign-source-data.html
No, my conceptualization of identity has nothing to do with the administrative process.
Entity exists and identities associated with it exist without any respect to administrative process what so ever.
Not sure I understand how you can say that without changing the meaning of the process you are using to describe identity. Observance and noting attributes is administration within your mind’s file system. The primary “Entity” in figure one is an administrative construct, by your very definition and effort to avoid the philosophical constraint of existence. There is a mirrored image of that “Entity” just to the left of your diagram… and it is representative, specifically, of a Human Individual. Every attempt to identify/describe that source “Entity” is administrative… it is not the thing being identified/described.
Systems management continues to leave this “sovereign source authority” out of its design. It is a crucial component… THE crucial component… to make our technical/social/economic systems function as they should.
You are right to avoid the “existence” conversation. I am. You are. All that matters is that we need the value and leverage of participation with our systems to correlate in the right way… and to do that, we must recognize the sovereign source in the exchange.
Do you see that happening anywhere in the identity conversation?
Could you define the term “administrative”?
A data process that documents/defines/specifies that which the data correlates to for managed purposes. Such as; registering a live birth is an administrative process.
Then you are mistaken. Entity’s existence in this context has nothing to do with administrative construct.