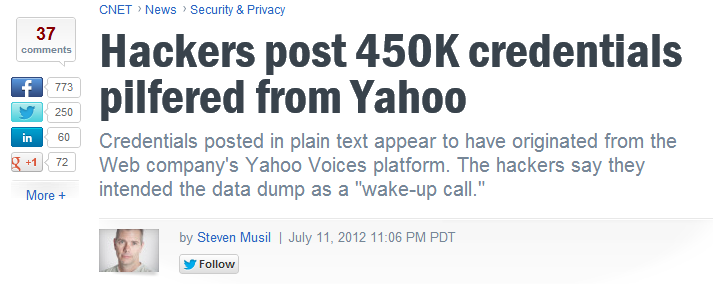
Lot’s of articles appeared on the Yahoo! Voices’ password leakage on the 11th.
Many people seem to be assuming that Yahoo!s password has been leaked, but to me it seems a little different.
According to the press articles[1], it seem the password has been extracted from a service called Yahoo!Voices using SQL Union injection. The mail address that were leaked included not only Yahoo!but also hotmail, etc. This actually is a very wiered case. Why?
Yahoo! Voice is a relying party to Yahoo! and is federating the authentication. This means that Yahoo! Voice should not have any password to be stolen. This is a contradiction. So, I went onto researching what Yahoo! Voice really is.
Origin of Yahoo! Voices
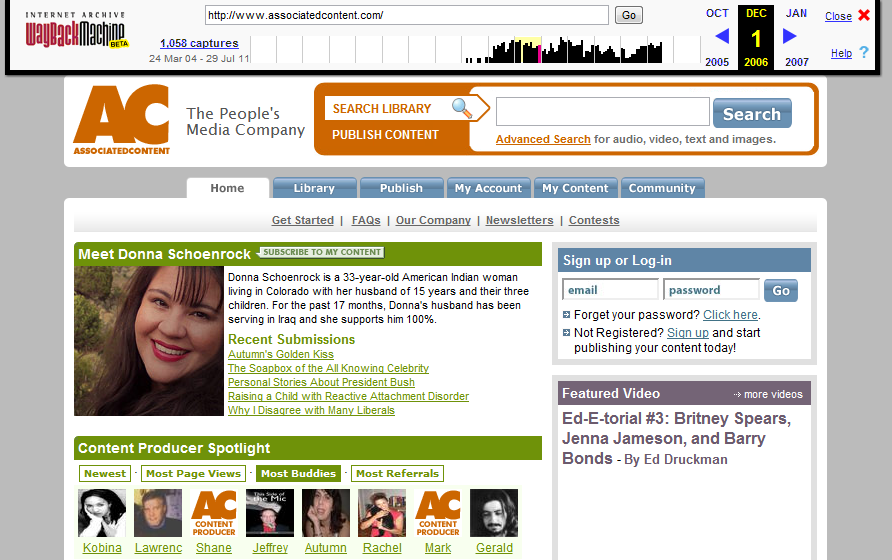
Yahoo! Voices is a user generated content publishing platform that is offered by Yahoo!. It started its life as “Associated Content” under the domain www.associatedcontent.com in January 2005. In May 19, 2010, Yahoo! bought this company at around US$90M [2] and renamed it to Yahoo! Voices.
Looking at the web site in Dec. 2006, it is clear that it was having users register email/password pair and write articles using that.
That is, in the Associated Content service, there used to be the email/password pair. This is what was leaked. And this is why only 5% of them actually matches with Yahoo!’s Identity Provider’s data. (Note: This also explains why there were hotmail address in the leak. Yahoo!’s Identity Provider does not accept hotmail account till now so it cannot exist.)
Typical example of “Home Brewed Password System” incident
Assuming the above is correct, then this is a typical example of “home brewed authentication system managed by non-professionals”. This is a consistent pattern that we have been seeing in similar incidents[3]. What is unfortunate in the Yahoo!’s case is that the site was offered under the same brand as that was providing authentication service. Saying that it was done by the acquired company and has nothing to do with the security level of the Yahoo!’s authentication service would probably not impact the fact that the press and normal people’s impression that “Yahoo!’s password leaked”. Thus, Yahoo!’s authentication business gets negative impact.
Two lessens we can learn from this incident are:
- Do not mange your own authentication system unless you really know what you are doing. Doing it right is difficult. Use the federated authentication and through the passwords away.
- If you are buying a service that does password authentication and start offering it under your brand, do the due diligence carefully. Use a federated authentication and through the password of the service away. Make sure that there is no remaining of passwords.
Revision History
- 2012/7/12 20:17 (CDT) Original version in Japanese. Written in Tokyo.
- 2012/7/14 10:39 (CDT)English version. Written in Denver, Co.
[1] Source: CNET. According to it, the file has dbb1.ac.bf1.yahoo.com in it.
[2] Source: Crunch Base ( http://www.crunchbase.com/company/associatedcontent )
[3] On the other hand, LinkedIn case was indeed a leak from the IdP. Thus, we need a way to find out which IdP is operated by professionals and which is not. For this, a rating under a trust framework should be useful.